This incident response method segregates the infected systems – This incident response method segregates infected systems, standing as a crucial component in safeguarding networks from the damaging effects of malware. By isolating compromised systems, organizations can effectively contain threats, preventing their spread and minimizing potential damage. This comprehensive guide delves into the significance, implementation, and challenges associated with this critical cybersecurity measure.
As malware continues to evolve in sophistication, incident response plans must adapt to address the growing threats. This guide provides valuable insights into the process of isolating infected systems, restoring compromised systems, analyzing malware, and developing effective incident response plans.
By leveraging this knowledge, organizations can enhance their cybersecurity posture and respond swiftly and effectively to security breaches.
1. Isolation and Containment
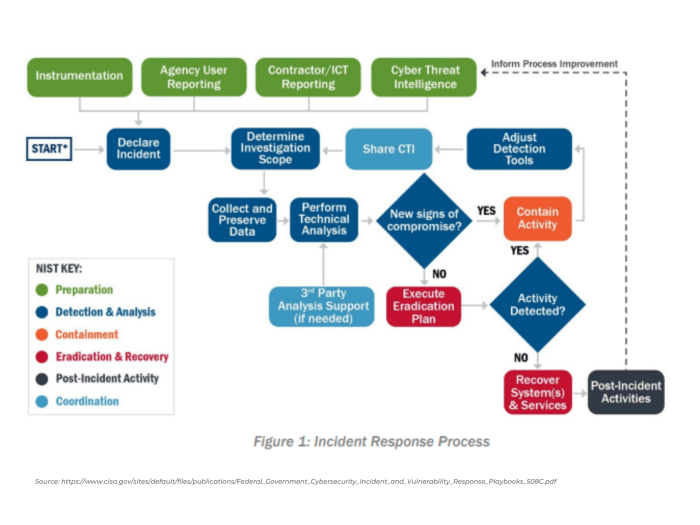
Isolating infected systems from the network is crucial to prevent the spread of malware. This can be achieved through various methods, including VLANs, firewalls, and air-gapping.
VLANs (Virtual Local Area Networks) create logical network segments that isolate traffic between different devices, while firewalls block unauthorized access to and from the network. Air-gapping involves physically disconnecting infected systems from the network, providing the highest level of isolation.
Challenges of Isolating Infected Systems
- Complex network environments may make it difficult to identify and isolate all infected systems.
- Malware can spread quickly, making it challenging to contain the infection before it reaches other systems.
2. System Restoration
Restoring infected systems to a clean state involves removing malware and repairing any damage it may have caused. Common restoration methods include reimaging, file recovery, and patch management.
Reimaging involves wiping the infected system and reinstalling the operating system and applications. File recovery focuses on restoring individual files that have been corrupted or deleted. Patch management updates software and firmware to fix vulnerabilities that may have allowed the malware to infect the system.
Challenges of Restoring Systems
- Severely compromised systems may require extensive restoration efforts, including data recovery and hardware replacement.
- Malware can persist in hidden locations, making it difficult to fully remove and restore the system.
3. Threat Analysis and Remediation
Analyzing malware helps understand its capabilities and impact. This information is used to identify vulnerabilities that allowed the malware to infect the system and develop appropriate remediation strategies.
Remediation involves patching vulnerabilities, implementing additional security measures, and updating security policies. In some cases, it may also require modifying system configurations or replacing compromised hardware.
Challenges of Threat Remediation
- Persistent threats can evade detection and remediation, requiring advanced techniques and ongoing monitoring.
- Sophisticated malware may employ multiple evasion techniques, making it difficult to identify and remove.
4. Incident Response Plan: This Incident Response Method Segregates The Infected Systems
An incident response plan Artikels procedures for segregating infected systems and responding to security incidents. It defines roles and responsibilities of different stakeholders and establishes clear communication channels.
The plan should be regularly tested and updated to ensure its effectiveness and relevance. It should also include provisions for continuous monitoring and threat intelligence sharing to stay ahead of emerging threats.
Importance of Incident Response Plan, This incident response method segregates the infected systems
- Provides a structured approach to incident response, reducing chaos and improving coordination.
- Ensures timely and effective segregation of infected systems, preventing further damage.
Query Resolution
What are the benefits of isolating infected systems?
Isolating infected systems prevents the spread of malware within a network, minimizes potential damage, and facilitates effective containment and remediation efforts.
What are the challenges of restoring compromised systems?
Restoring compromised systems can be challenging due to data loss, system instability, and the need for specialized recovery tools and expertise.
How can organizations develop effective incident response plans?
Organizations can develop effective incident response plans by defining clear roles and responsibilities, establishing communication channels, and conducting regular testing and updates.